Find the best CRM Software
Compare Products
Showing 1 - 20 of 3396 products
Sort by
Reviews: Sorts listings by the number of user reviews we have published, greatest to least.
Sponsored: Sorts listings by software vendors running active bidding campaigns, from the highest to lowest bid. Vendors who have paid for placement have a ‘Visit Website’ button, whereas unpaid vendors have a ‘Learn More’ button.
Avg Rating: Sorts listings by overall star rating based on user reviews, highest to lowest.
A to Z: Sorts listings by product name from A to Z.
Salesforce Sales Cloud
Salesforce Sales Cloud
Grow your revenue and profits with intelligent sales automation with Sales Cloud. Help every rep be more efficient. Close more deals. Collect cash faster. Boost growth and profit with intelligent automation and integrated tools fr...Read more about Salesforce Sales Cloud
Thryv
Thryv
Thryv is an all-in-one business management solution designed to help small businesses with essential business functions. With Thryv, business owners can expand their online presence, improve any customer relationship, and streamli...Read more about Thryv
HubSpot Sales Hub
HubSpot Sales Hub
Supercharge your sales process with Sales Hub, a powerful and easy-to-use sales CRM that includes sales engagement tools, configure-price-quote (CPQ) functionality, and robust sales analytics and reporting for growing teams. Optim...Read more about HubSpot Sales Hub
Shape
Shape
Shape's cloud-based solution offers tools designed to manage online marketing and promotions, capture leads from online sources, organize sales pipelines, connect with customers and automate everyday tasks. Shape is suitable for b...Read more about Shape
Talk with us for a free
15-minute consultationSoftware Advice is free because vendors pay us when they receive sales opportunities.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
Meet Eric, a software expert who has helped 1,534 companies select the right product for their needs.
Talk with us for a free
15-minute consultationSoftware Advice is free because vendors pay us when they receive sales opportunities.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
This allows us to provide comprehensive software lists and an advisor service at no cost to you.
Tell us more about your business and an advisor will reach out with a list of software recommendations customized for your specific needs.
STEP 1 OF 4
How many are in your organization?
Claritysoft CRM
Claritysoft CRM
FrontRunners 2024
Claritysoft is a cloud-based customer relationship management (CRM) solution designed for midsize and large enterprise businesses. It offers sales automation, customer service and support, marketing automation and social CRM withi...Read more about Claritysoft CRM
Topline
Topline
*What is Topline?* Topline OS is an all-in-one growth operating system that brings together all the tools you need to run and grow your business in an easy to use, modern platform. It's packed with features like a complete CRM to ...Read more about Topline
TOP PRODUCER
TOP PRODUCER
Top Producer is an all-in-one business management platform designed specifically for real estate agents and teams. Grow your database and convert more leads with cutting-edge lead generation and marketing automation. Smart follow-...Read more about TOP PRODUCER
FreeAgent CRM
FreeAgent CRM
FreeAgent CRM is a fully-featured CRM that helps your team get organized, gain visibility into day-to-day work, and get more done with a powerful, easy-to-use sales platform your sales team will actually love. Work smarter and f...Read more about FreeAgent CRM
iHomefinder
iHomefinder
iHomefinder has been a leading innovator in real estate technology for over 20 years. Our solutions are available only to active licensed real estate agents and brokers, and account activation requires MLS membership verification....Read more about iHomefinder
OA Mobile
OA Mobile
FrontRunners 2024
Our primary goal is too make your life easier. OA Mobile is like having an extra employee. We will do most of the work for you. After 32 years and thousands of customers we know how to make a CRM work for you. OA Mobile is a CR...Read more about OA Mobile
SugarCRM
SugarCRM
SugarCRM is a Customer Relationship Management (CRM) platform, expertly crafted to enhance interactions with prospects and customers while accelerating sales success. Renowned for its cost-effectiveness, this potent solution enabl...Read more about SugarCRM
LeadSquared
LeadSquared
LeadSquared is a cloud-based marketing automation and customer relationship management (CRM) solution for businesses of all sizes. It serves clients in industries such as finance, e-commerce, education, health and wellness, market...Read more about LeadSquared
BNTouch Mortgage CRM
BNTouch Mortgage CRM
BNTouch Mortgage CRM is a fully integrated digital mortgage system, CRM, marketing, and POS tool offering a comprehensive mortgage business growth platform for loan officers and mortgage companies. BNTouch Mortgage CRM includ...Read more about BNTouch Mortgage CRM
FunnelMaker
FunnelMaker
FunnelMaker is a cloud-based customer relationship management (CRM) solution designed for businesses of all sizes. The solution offers a user dashboard and helps in automatic sales tracking, email tracking and opportunity manageme...Read more about FunnelMaker
BoomTown
BoomTown
Boomtown provides marketing and sales automation solutions for the REAL ESTATE industry. Through Boomtown, brokers can select and customize a lead generation website, track and nurture leads, and monitor team success and sales. Th...Read more about BoomTown
Rolldog
Rolldog
Rolldog is a Customer Relationship Management (CRM) solution, with the perks of Sales Enablement all rolled into one. Rolldog helps companies manage their business relationships, increase revenue, and boost sales & marketing effec...Read more about Rolldog
monday sales CRM
monday sales CRM
FrontRunners 2024
Built on top of monday.com Work OS, monday sales CRM is a no-code, customizable solution that empowers managers and sales teams to take control of their entire sales cycle - from lead capturing and sales pipeline management to pos...Read more about monday sales CRM
Creatio CRM
Creatio CRM
Creatio is a global vendor of a no-code platform to automate workflows and CRM with a maximum degree of freedom. Creatio offering includes a no-code platform (Studio Creatio), CRM applications (Marketing, Sales and Service), indus...Read more about Creatio CRM
SalesNOW
SalesNOW
SalesNOW by Interchange Solutions Inc. is a cloud-based customer relationship management (CRM) and sales force automation solution that allows sales teams, management and executives to manage aspects of sales cycle including conta...Read more about SalesNOW
LeadMaster
LeadMaster
LeadMaster is a SaaS-based all-in-one lead management solution that offers capabilities to capture, track and follow up with leads. The solution comprises of integrated modules for sales force automation, customer relationship man...Read more about LeadMaster
Popular Comparisons
Buyers Guide
Last Updated: March 16, 2023What is CRM software?
Customer relationship management (CRM) software is software that automates and manages the customer life cycle of an organization. It is usually used by the sales team, sales reps, and call center reps to maintain contact with customers and quickly respond to their needs.
Note: Specific sales CRM platforms have features that are optimized for sales teams.
Basically, if you work with a lot of customers, a CRM is your team's best friend. Not only will it help you manage your data, a good CRM makes your customers' experience fluid and effortless.
Here's what we'll cover:
Benefits of CRM software
CRM software provides your business with several tangible benefits, including:
Customer data management: Most products provide a searchable database to store customer information (e.g., contact information) and relevant documents (e.g, sales proposals and contracts). While most CRMs offer this functionality, it can also be incorporated into other industry-specific systems. For example, contact management is a core component of salon management software.
Interaction tracking: A CRM solution documents customer interactions, such as conversations held by phone, in person, through live chat, email, or other channels. These interactions can be logged manually, or automated with phone and email system integrations. Some systems can also track interactions on social media platforms including Facebook, Twitter, and Google.
Workflow automation: This standardizes business processes, usually through a combination of task lists, calendars, alerts, and templates. For example, once a task is marked as complete, the CRM system might automatically create a task for the next step in the process.
Reporting: Management can use CRM tools to track performance and productivity based on activities logged in the CRM system—for instance, how many new contacts were added to the database that day, or how much revenue was generated. These tools can also be used for sales forecasting, such as for the next-quarter sales pipeline, lead management, scoring, and analyzing customer satisfaction.
Competitive advantages of using CRM software
Whatever business you're in, chances are you frequently have to deal with customers, prospects, or other important contacts. When it comes to these interactions, CRM software gives you an advantage over your competitors by helping you with the following:
Scale your business: If you only have 100 contacts to deal with, then you might be able to keep all of their information straight using a simple Excel spreadsheet, or even pen and paper. Larger companies, however, deal with thousands or potentially millions of contacts and customers, which require customer relationship management software in order to keep that information well-organized and accessible
Operate more efficiently: When everyone in your company has access to your customer and contact data, you can deal with those customers more efficiently and avoid the dangers of over- or under-contacting them. You can also track those customer interactions and analyze that data for more efficient resource planning and optimize the sales process.
Compete with superior customer satisfaction: Staying in the right amount of touch with your customers, and using the communication method they prefer, lets you stay on top of their needs and concerns in a way that stands out. Superior customer service, focused on providing the best possible customer experience, will allow you to seriously compete against other businesses.
Businesses sizes using CRM software
CRM systems are used by many businesses, across a variety of industries, so there's no "typical" buyer. In general, though, you'll fall into one of the following categories:
Single user: The smallest businesses consist of only one owner/employer, such as real estate agents, freelancers, or independent contractors.
Small business buyer: These are companies with two to 100 employees and typically have no IT department.
Midsize business buyer: These are companies that have 101-1,000 employees and tend to have an IT department.
Large business buyer: These are companies that have more than 1,000 employees and have a dedicated IT department.
Software related to CRM
CRM can be divided into several related subcategories of software, all of which focus on improving your relationship with your customers:
Sales force automation (SFA) software: Helps you manage your sales team's activities, and helps the sales team close more deals by keeping thorough, accurate records of their interactions with all sales prospects.
Marketing automation: Provides tools that helps marketers reach out to potential customers through a variety of channels—especially email—and tailor messages to them.
Customer experience software: Combines frontline customer service applications, such as live chat and tools for self-service knowledge bases, with tools that connect departments in order to oversee individual customer experiences.
Help desk software: Stores customer information in a searchable database, tracks interactions, and automates the issue resolution process using an issue tracking system. It can be used for either external customers (consumers or businesses that have purchased goods or services from your company) or internal customers (employees).
Live chat software: Allows you to have real-time conversations with website visitors in order to improve customer service, help increase online sales, and encourage repeat business by providing customers with precisely what they want.
Features guide
A list of common CRM features
When comparing CRM software, it's important to understand the functionality included in each. The most common functions of these systems are listed in the table below:
Contact and opportunity management, sales forecasting, pipeline analysis, and reporting. | |
Lead management, email and event marketing, marketing analytics, and campaign management. | |
Trouble ticketing, self-service solutions, case management, customer experience platforms, live chat, and surveys. | |
Trouble ticketing, knowledge management, self-service, and IT asset management. |
Feature details and examples
Sales force automation: Provides you with the tools to streamline and manage your sales team's performance. Also gives your salespeople the ability to more efficiently track their prospects and customers with functions such as contact management, lead management, opportunity management, pipeline management, forecasting and territory management.
![]()
Opportunity tracking in Salesforce (Source)
Marketing integration: This feature allows you to automate your marketing campaigns through the CRM system. It enables you to attract new visitors and customers, score customers as leads that can be nurtured along the sales pipeline, deliver marketing and promotional materials through various channels (e.g., via email marketing, social media etc.), obtain analytics about customers to improve marketing efforts and automate repetitive, time-consuming manual tasks.
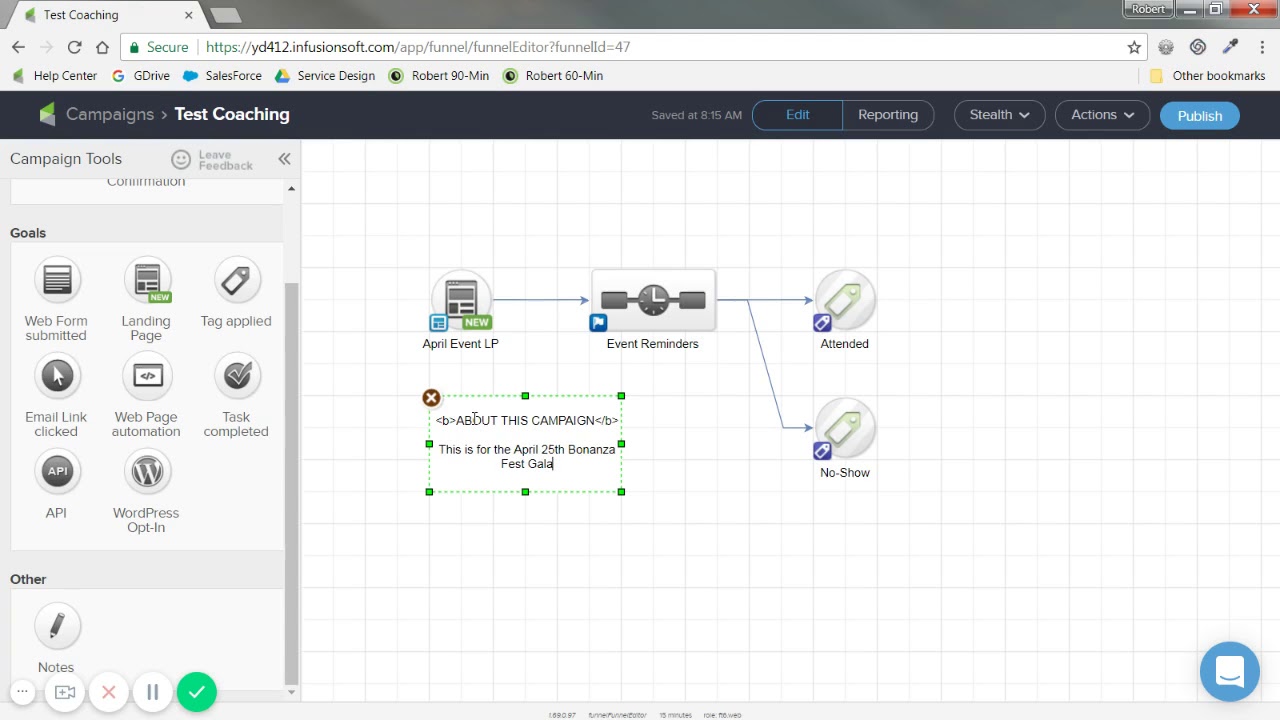
InfusionSoft's campaign builder page (Source)
Customer service and support: This functionality consists of a set of tools that allows you to cater to customers' needs by tracking their interactions with your company to focus on creating the best possible customer experience for each individual. Specifically, it allows customer service representatives to document, route, track, resolve and report on customer issues via a trouble ticketing system, using tools such as live chat, customer self service and multichannel management.
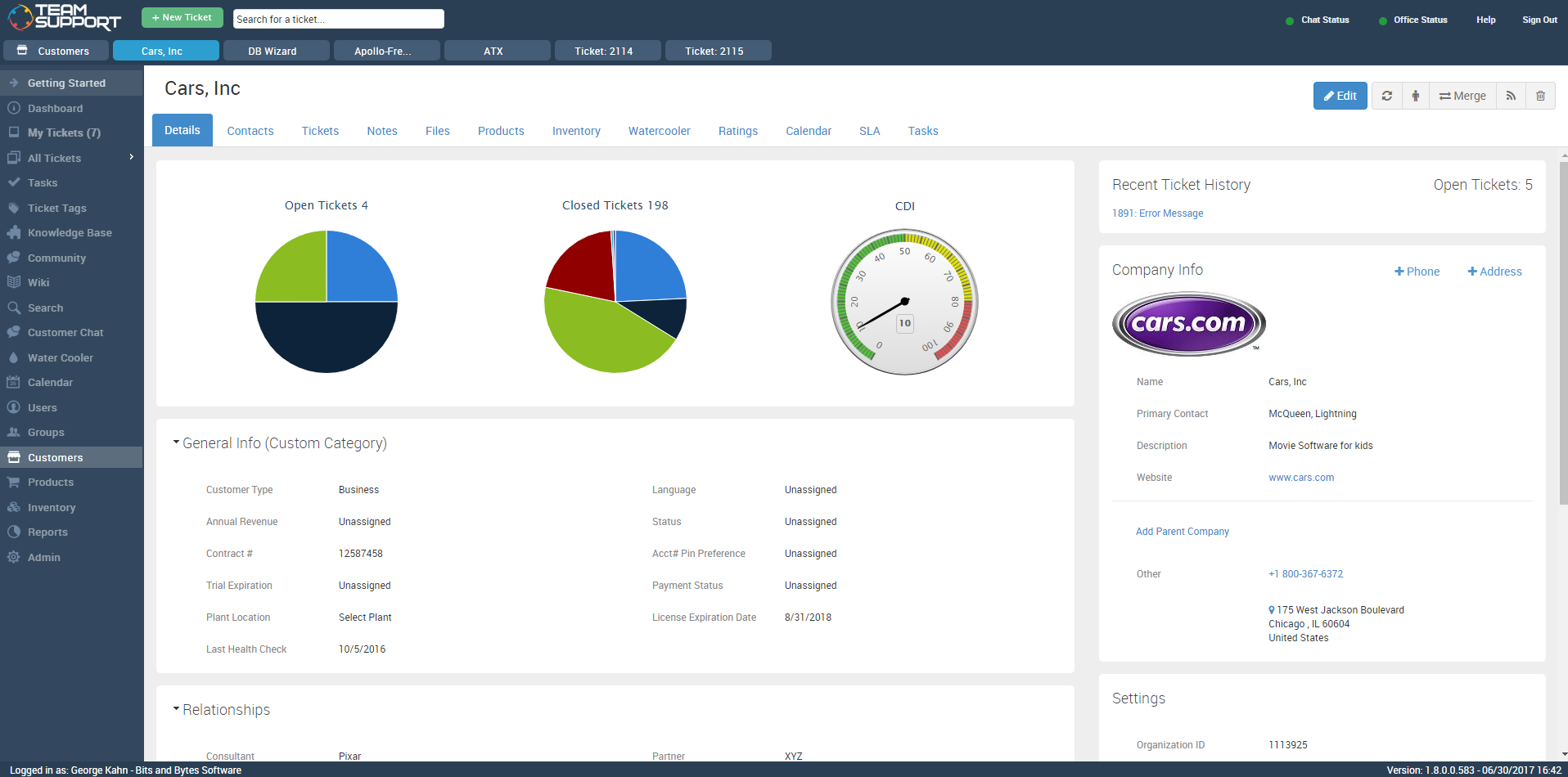
TeamSupport's customer management page (Source)
Help desk automation: This is similar to customer service and support in that it also focuses on creating the best possible individual customer experience. However, it is more focused on resolving IT issues, and the "customer" may be either external or internal (i.e., employees who need help with IT issues). Help desk automation involves the creation of an electronic ticket that customer service representatives track and associate with customer profiles that include contact information and, potentially, purchase history or assets.
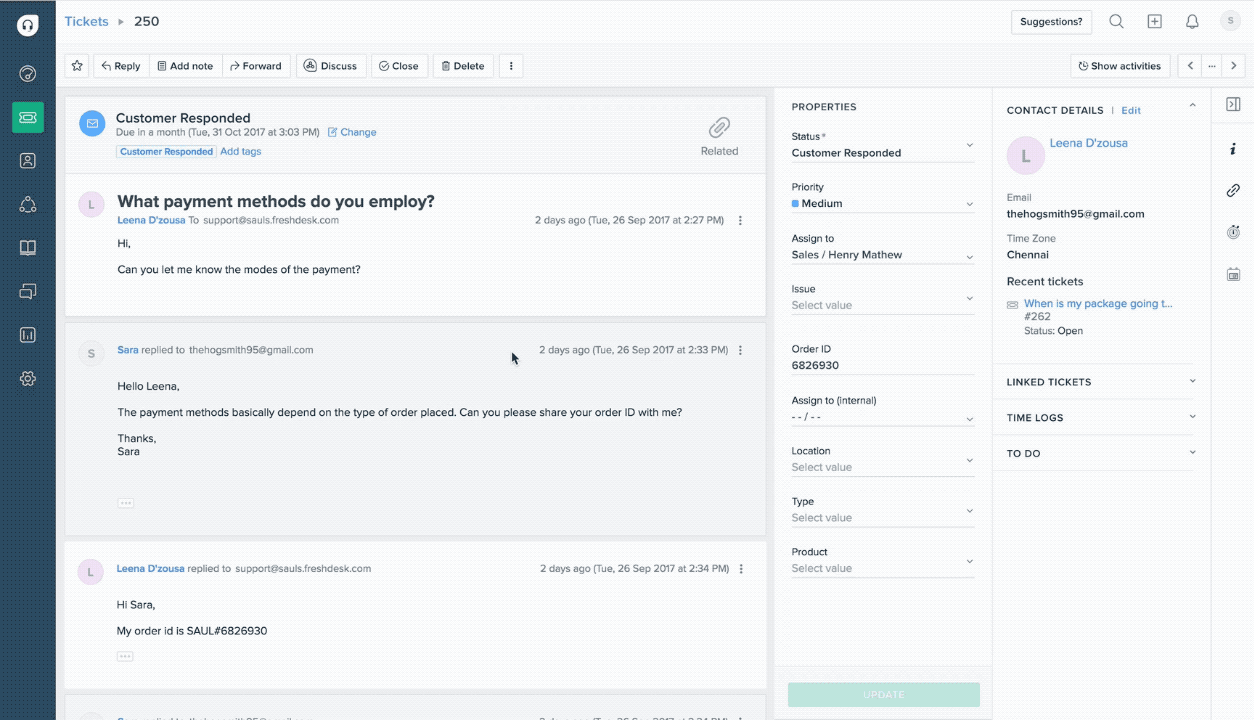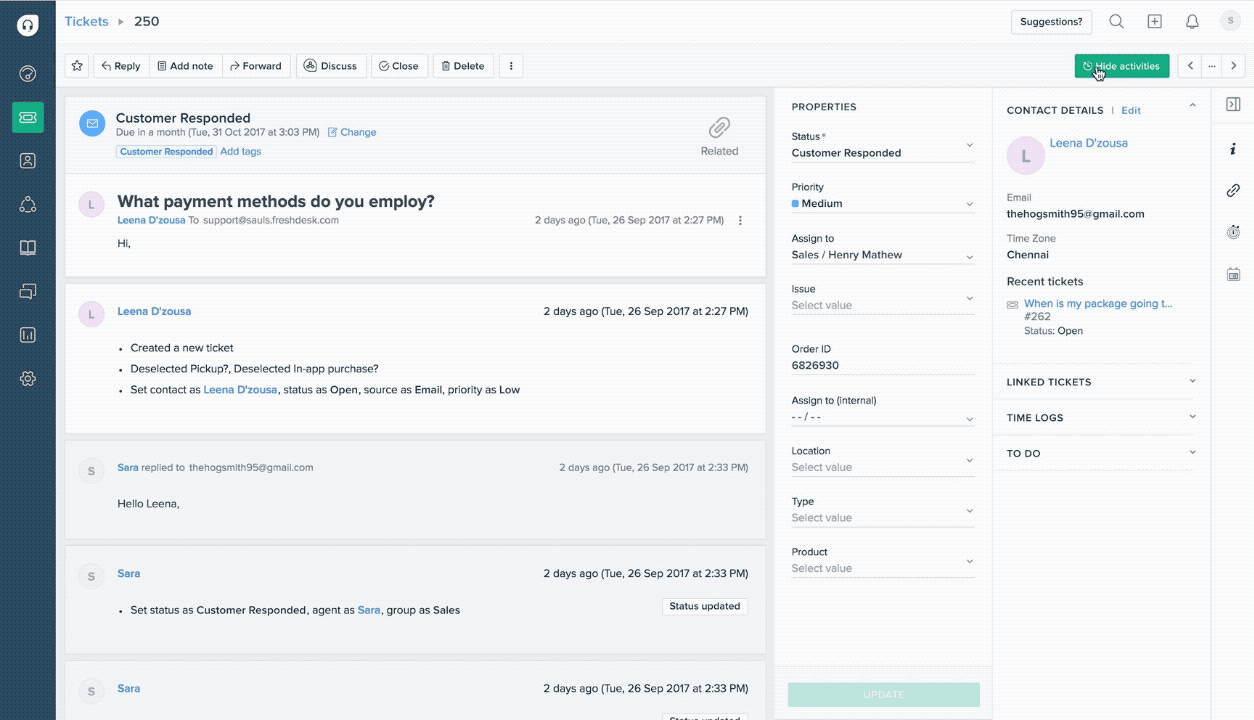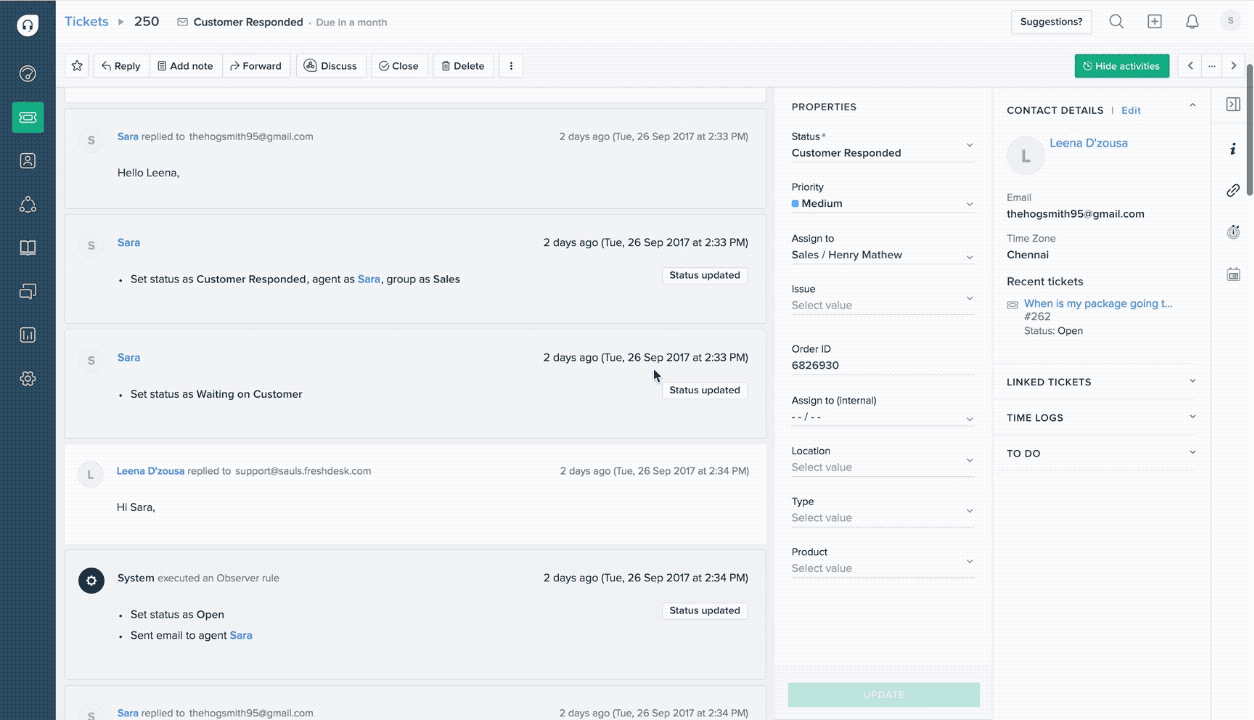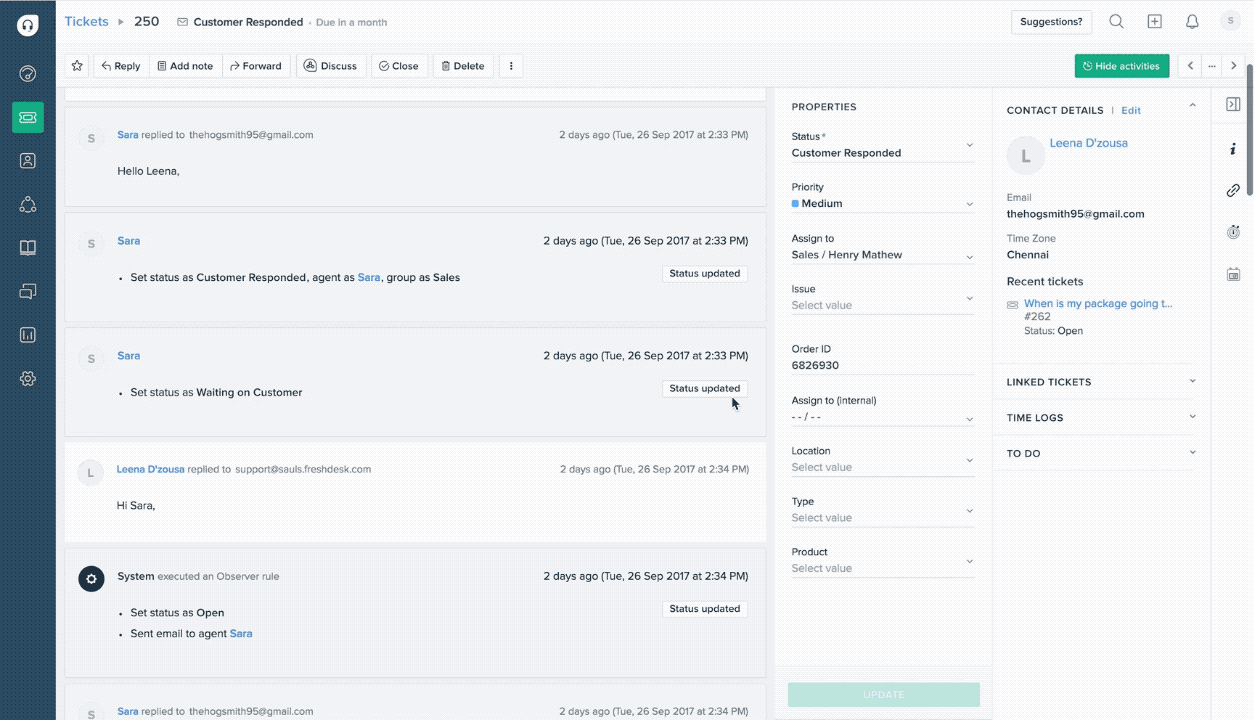
Freshdesk's ticket activity history
CRM buyers' top requested features
The buyers we've helped at Software Advice tend to be looking for some of the more basic aspects of customer relationship management systems. Their top-requested features, by far, are contact management, interaction tracking and scheduling/reminders-all defining features of CRM software. The more specialized features are, the less buyers tend to request them.
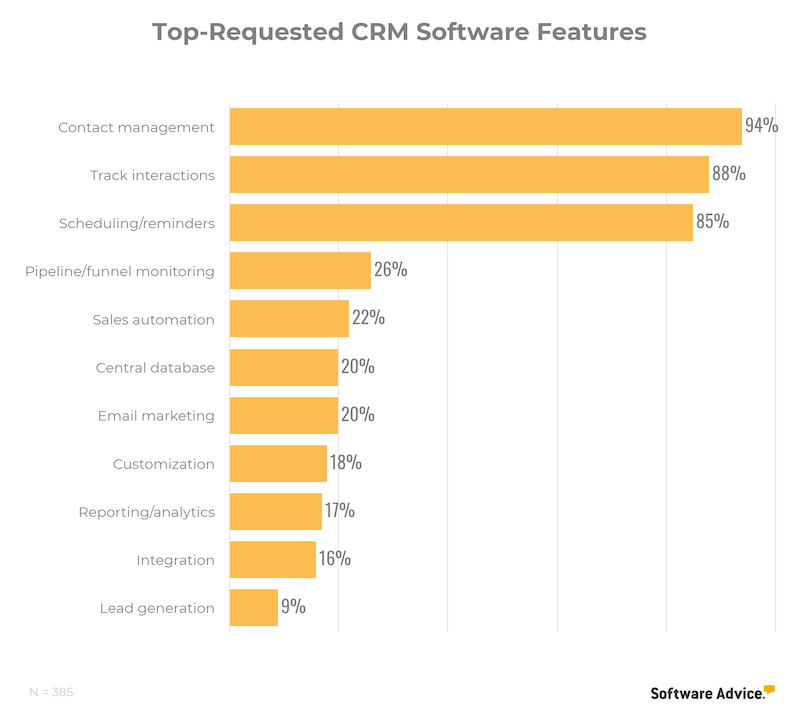
The CRM software features you really need
Certain CRM features are more critical than others depending upon your business' stage of growth. Here are some of the most crucial features for different business sizes (see the "Business Sizes Using CRM Software" section of this guide for business size definitions):
Single user | Contact database: Your CRM database helps you manage and track each customer interaction, saving time by eliminating the need for complex spreadsheets or tracking your contacts through pen and pencil. |
Small business buyer | Sales automation: Helps you manage sales activities down to individual sales reps. It can also generate sales forecasting and provide insight into your sales pipeline. |
Midsize business buyer | Marketing automation: Helps automate your lead generation and nurturing funnels, provides insights and assists with targeted marketing campaigns. |
Large enterprise business buyer | Customer service functionality: Allows your customer service representatives to fully track and manage the customer journey and make sure they're receiving the proper amount of care and individuality along the way. |
Pricing guide
How CRM software is priced and hosted
CRM software is typically hosted online and licensed out to companies on a per user, per month basis, alongside one-time implementation costs—otherwise known as a Software-as-a-Service (Saas) or online CRM model. Some vendors may have a flat monthly fee regardless of the number of users, though it varies between different market segments. For example, sales force automation is almost universally sold per user/month, while marketing automation often is sold via a flat monthly fee. However, this flat fee is increasingly uncommon.
The per user/month costs across the SaaS market average from around $50-$90 per user/month, depending upon required functionality, though it can also be much cheaper (e.g., $10-$15 per user/month) and much more expensive (e.g., $200-$300 per user/month) depending on the vendor. Additionally, there are a variety of free CRMs, but these will offer limited functionality.
The flat monthly fees for more specialized systems tend to be more more expensive, starting at around $200/month, but can scale up to around $3,000-$4,000/month for more robust systems.
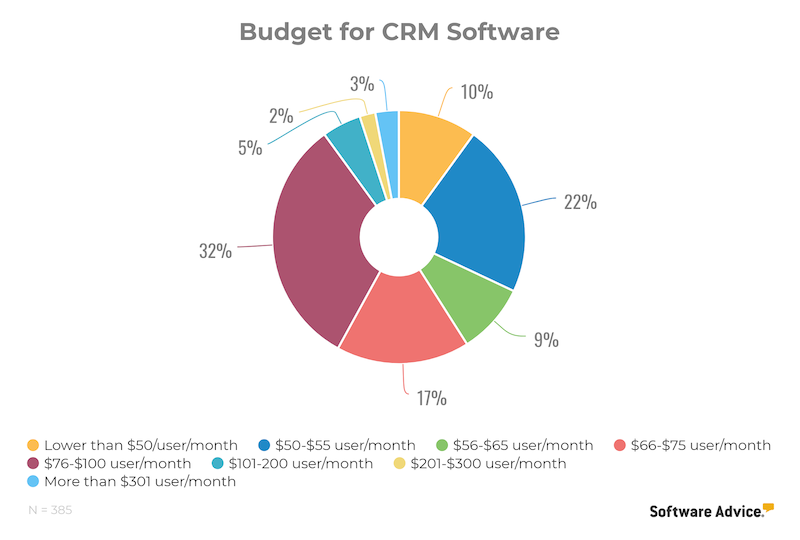
What businesses typically budget for CRM
Based on an analysis of the CRM software buyers we speak to, business budgets for a CRM solution vary widely. The highest percentage of buyers (about 32 percent) budget for $76-$100 per user, per month, while only 3 percent are willing to budget more than $301/user/month.
Please note that these prices do not include any potential up-front fees, such as installation and training.
Hidden costs of CRM software
Because it is such a staple of so many industries and businesses, CRM software vendors make their money more through volume than through nickel-and-diming customers. As such, there are few hidden costs, with one notable exception: implementation.
The majority of SaaS CRM systems can run without dedicated IT support, either internally or from the vendor, so extra costs come out of paying the vendor to install the software and provide training sessions for key users. Depending on the vendor and the system, this cost can range from a few hundred to a few thousand dollars.
An on-premise CRM solution will require a dedicated IT team in order to maintain the servers and administration duties.
FAQs
What are the key functions of CRM software?
As discussed in the "Benefits of CRM software" section above, CRM software provides several key functions for your marketing teams, including:
Contact management: Manage and store customer, client and prospect data so you can contact them at the right time using their preferred method of outreach.
Interaction tracking: Keep detailed notes on each employee's interactions and email campaigns with customers, clients, and prospects for the future use of anyone at your company.
Workflow automation: Create task lists, reminders, calendars, alerts, and templates that will help streamline your dealings with customers.
Reporting and analytics: Generate reports that track and analyze the performance and productivity of your company and employees based on the data in the CRM system.
What should I ask vendors when evaluating CRM products?
When researching CRM vendors, don't just rely on the information they provide. Request a demo, where a representative walks you through the software and its various features.
However, don't let this demo just be a sales pitch. Be sure to ask important questions, such as:
What parts of the software do users most frequently report problems with?
Don't just focus on functions vendors rave about, but ask what tends to be challenging for users. This will also enable you to gauge just how frank the representative is willing to be with you about their product. If a key feature for your business needs and sales pipeline is a pain point for other customers, it likely will be for you, too.
What are the set-up costs for the software?
Most vendors will price CRM software based on a "per user, per month" model, but there are frequently up-front costs that come with implementation.
How likely are we to require tech support in order to set up, implement, and/or use the software?
If you have a small or no IT department, it will be important to know whether or not you'll require (potentially costly) tech support in order to implement and maintain the software.
How easy will it be to add features at a later date?
As you become more familiar with a given system, you may want to add more complex functions, such as marketing integration or reporting and analytics. Check to see whether there are any hidden costs or challenges associated with adding features later on. An integration to your social media management system is a possible example here.
Is there a mobile app?
Your team likely works from smartphones or tablets, therefore the type and cost of the CRM mobile app could be important for your business. Your team can follow up with customers quickly and sometimes in real time, make phone calls while on the go, check their email and social media interactions, and overall improve the employee experience with an intuitive mobile app.
Be sure to ask if the mobile app is optimized for Android or iOS devices—whichever your team uses.
What's the difference between marketing automation and salesforce automation?
CRM vendors offer a lot of applications with their products, and jargon is commonly used to describe them. We've demystified much of this in our article, "The ABCs of CRM: A CRM Terminology Primer."
What if my company doesn't differentiate between sales and marketing?
Many companies these days have call centers and marketing teams that communicate with such frequency that they often function as one unit, an alignment called "smarketing." You can find out how this influences software choice in our article, "How 'Smarketing' Paired With Software Can Help Align Sales and Marketing."
How do I get my team to adopt CRM software?
One of the biggest challenges of purchasing CRM software is getting your team to use it—especially sales teams that are often attached to practices they don't want to interrupt with new technology.
What are some drawbacks I should watch out for?
A CRM solution isn't a magic cure-all for companies that have problems due to their own dysfunctional business processes or poor corporate hygiene. Some businesses think that buying software will fix a disorganized sales team, an inexperienced marketing team, or poor data entry, but in reality the CRM tools may just scale up and worsen existing problems.
For CRM software to work successfully for your company, you need to make sure that the teams and individuals who will use the CRM platform are equipped to deal with the increased customer base that the software may bring on board.
Tips and tools
Build a business case for CRM software
Purchasing CRM software will generate a solid return-on-investment (ROI) for your business. You can use this ROI as a selling point when trying to justify the purchase price, as we explain in detail in our article, "How to Build a Business Case for CRM Software."
Relevant articles
Here are some recent articles about CRM software you should check out: